All
the interfaces faster
than Fast Ethernet or ASUS RT-N15
16 August 2009 14-48
Introduction
Fast Ethernet and Wi-Fi 802.11g have already become a common thing. But now Gigabit Ethernet and 802.11n begin to replace them in the SOHO segment. Today we are going to talk about such device - ASUS RT-N15, a router supporting both Gigabit Ethernet and 802.11n draft standards. If gigabit LAN ports can be considered as an ordinary feature, a gigabit WAN port is a characteristic that can be found not in every device. Yet this does not mean that the routing speed will be as high as that. It is quite possible that the speed will just about 100 mbps point. Let’s check it in our tests.
Exterior Design
The case of ASUS RT-N15 is made of white plastic with silver insert and rounded corners. The device will fit well on a table but it will need some additional fixtures for mounting on a wall or in a rack.

On the side panels there are the device model name and embossed vendor name. Besides, there are small vent holes at the bottom of the case.

The device has a turning stand for more stable positioning on the table and labels with a lot of information.

As the router can be positioned upright only, on the top of the case we can find additional vent holes and the model name.

On the front panel there are only LEDs indicating device and port status.

The rear panel has five ports for RJ-45 plugs (four LAN ports and one WAN port), power connector, and WPS and Restore buttons. The restore button is used for resetting and rebooting the router whereas the WPS button helps in establishing wireless network.

So, we got a full picture of how the device looks like. Now let’s examine its electronic components.
Hardware
RT-N15 hardware platform consists of a green printed circuit board. There are no large digital elements on the back of the board.

The most part of the front side is covered with metal screens, except three chips.

The operating memory is composed of two chips: 16 Mbyte EtronTech EM639165TS-6G and 16 Mbyte Samsung K4S281632K-UC60. Macronix 29LV320CBTC-90G with capacity of 4 Mbytes functions as a flash memory. Palmchip Surfboard is used as a processor. This can be found out via a command line.
Firmware upgrade
The firmware upgrade is a quick and easy process. To perform this you just need to select Firmware Upgrade category in Administration menu then choose the latest firmware file and click Upload button.
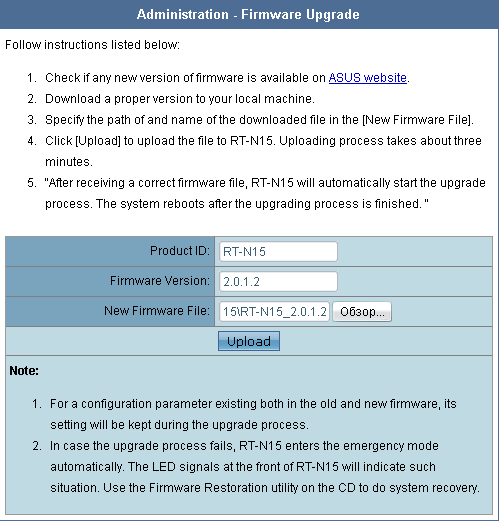
The uploading process is fully automated and takes about a minute.
After rebooting the router is ready for use.
Firmware restore
In case the current firmware is corrupted it is necessary to use the Firmware Restoration utility which can be downloaded from the vendor’s site. It must be mentioned that the restoration is possible if only the image of the operating system is corrupted. This can occur when, for example, the power goes down during the upgrade process. The restoration utility interface is available in different languages: English, Hungarian, Greek, Spanish, Italian, Chinese, German, Polish, Portuguese, Rumanian, Russian, French and Czech.
After the Restoration utility is installed on the computer, you need to launch it, choose the working firmware file and run the restoration process.
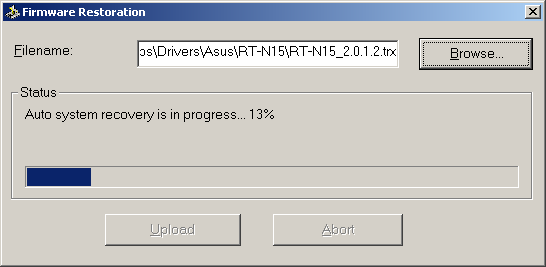
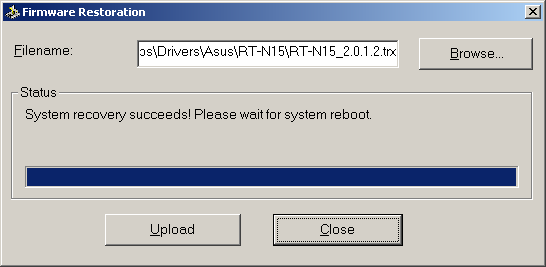
Yet, it must be kept in mind that this utility is not a cure-all solution even if used together with system resetting. The restoration of previously saved configuration from the corrupt file can destroy the system and an ordinary user won’t be able to repair it. Such a result can be reached with the help of the attached file. We strongly recommend not doing this. The only way out from the mentioned situation is to address to the Asus service center. Here we finish the review of the firmware restoration utility.
Web-interface review
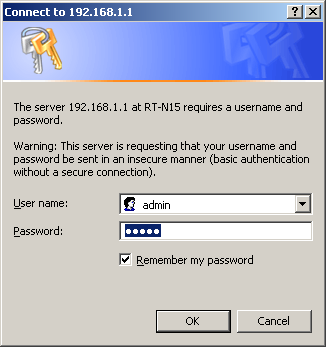
After connecting a computer or a notebook (laptop) to RT-N15 LAN-port, open browser and type a standard IP-address 192.168.1.1 in its address line. The user name and password are common for Asus network devices: admin/admin.
Upon successful authentication, the user finds himself in the router main page. Here he gets an opportunity to change the interface language. This feature can be very useful for those who are not good in English. Those who wish to study the Russian variant of web interface can address to the Russian version of this article.
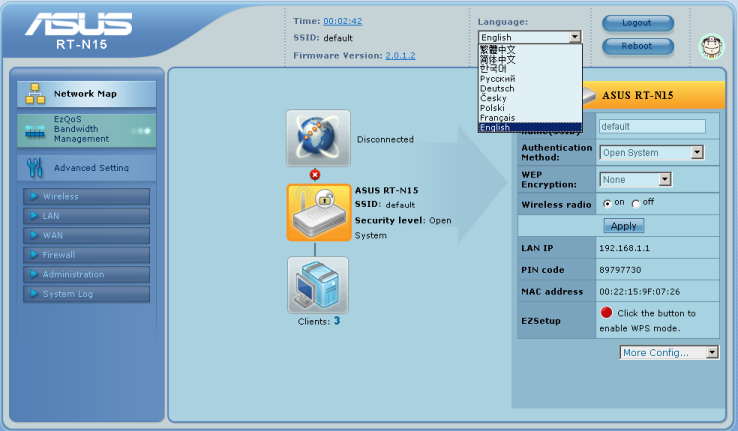
We are not going to describe RT-N15 web interface in detail but speak about the most interesting features. In the center of the main page the user can get a quick access to WAN, WLAN and LAN ports parameters by clicking on a corresponding icon. Let’s turn to the left frame of the web interface.
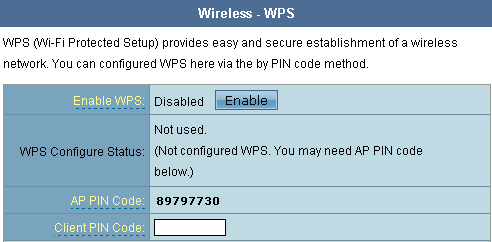
The Wireless submenu supports WPS (Wi-Fi Protected Setup) for easy adding of user devices.
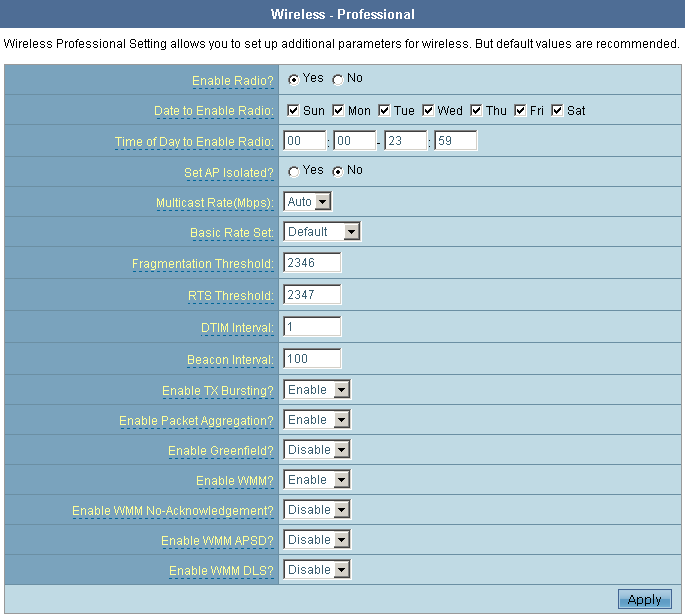
The Wireless-Professional submenu allows an administrator to set up additional parameters for wireless, for example the time interval during which RT-N15 will work with wireless clients.
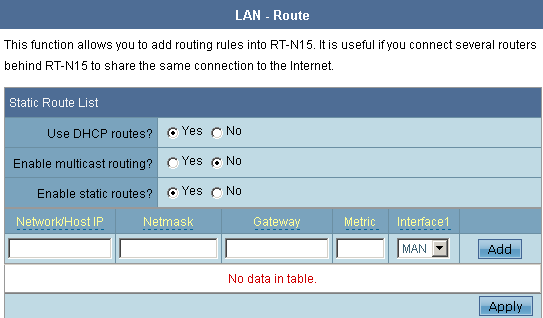
In LAN menu we take interest in the Route submenu which allows us to add static routes and enable multicast routing. It also allows receiving routes via DHCP.
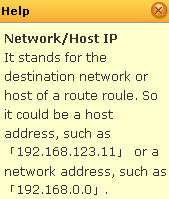
Here for the first time we felt like opening the manual to learn more about parameters of this tab that can be enabled or disabled as the information in Help document was not enough.
We downloaded the full manual ((E3515) RT-N15 manual.pdf) from the Asus web-site and found out that the described interface had nothing in common with the one at hand. It looked as if in this manual there were pictures from the guide of some other wireless router.
Let’s go to the WAN group. Here we can configure provider connection rules. Besides static and dynamic IP addresses WAN-port also supports PPPoE, PPTP and L2TP tunnels. You can specify local ports for IPTV translation as well.
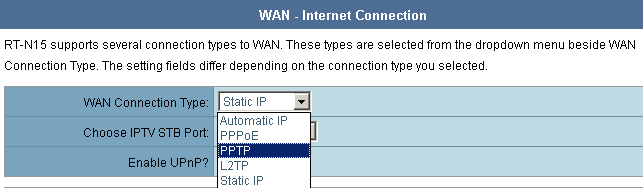
Here we also noticed the following features: when selecting PPTP the user can get a dynamic IP address of the physical interface or configure a static one; when selecting any connection type except PPPoE the user can’t specify some additional parameters like MTU. Besides, the administrator can select PPTP encryption parameters: no encryption, MPPE 40, MPPE 56 or MPPE 128.
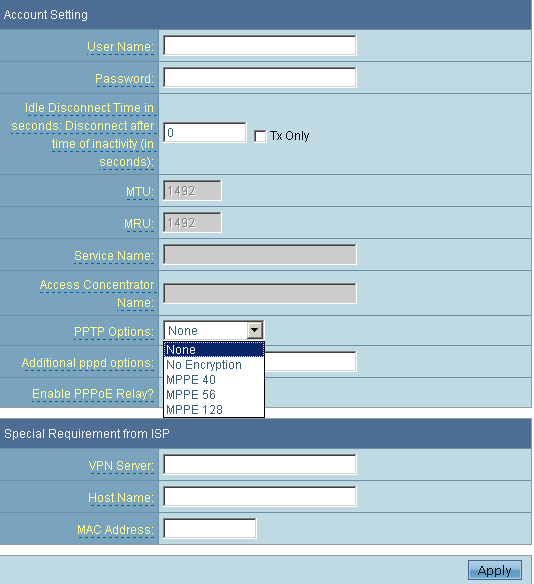
The QoS subcategory of WAN menu provides the administrator with means for bandwidth management. Actually, it is an opportunity to specify the priority of a certain service in comparison with the other flows.
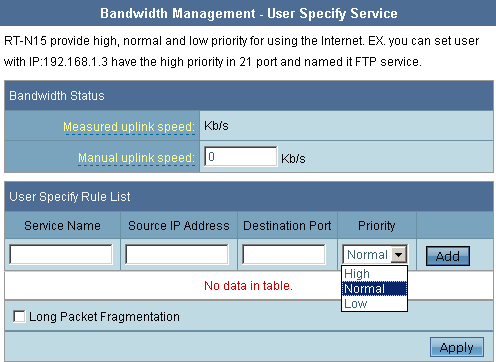
Besides selecting the priority for a certain service it is possible to specify the priority for the host, or to block it. To perform this it is necessary to go to the Network Map and click Clients button. The displayed list consists of all the clients found in the local network segment. Of course, we captured this network scanning by Wireshark utility. The file with transmitted packets can be found here. ASUS RT- N15 defines the presence of HTTP server and NetBIOS protocol support in scanned clients. It must be mentioned that there exists a risk that such actions of the router can activate personal security programs like Firewall or Antivirus.
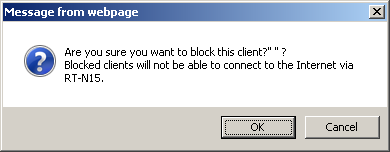
In the Firewall group the LAN to WAN Filter submenu arrested our attention by its additional options. Firstly, you can define the time-schedule when the filter will be enabled. Secondly, it is possible to not only filter the sockets but also specify the allowed TCP-flags.
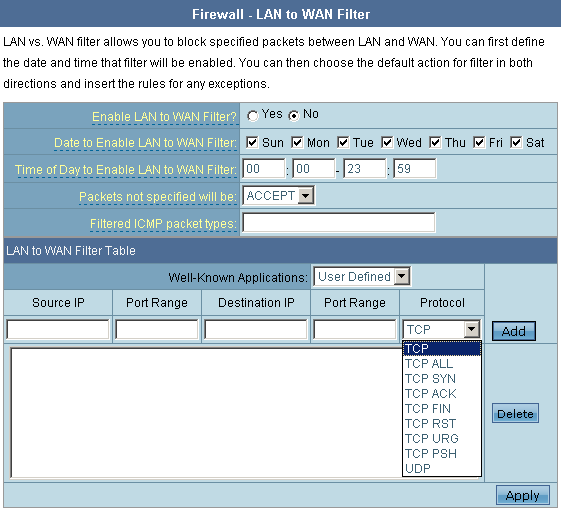
The status of NAT (enable/disable) can be changed in the Operation mode subcategory of Administration group by selecting an appropriate mode.
The brief review of the most interesting features of the router web-interface comes to an end. Yet, it should be mentioned that the process of saving and applying is very slow and can cause the router rebooting.
Command line interface
Despite the fact that ASUS RT-N15 firmware has telnet daemon protocol, it doesn’t run automatically with the system startup. You can do it manually from the hidden page http://192.168.1.1/Main_AdmStatus_Content.asp. Here it is possible to run not only services but also any system command you like. However, we are interested in access via telnet. Enter «/usr/sbin/utelnetd -d» command in the System command input field and click Refresh button.
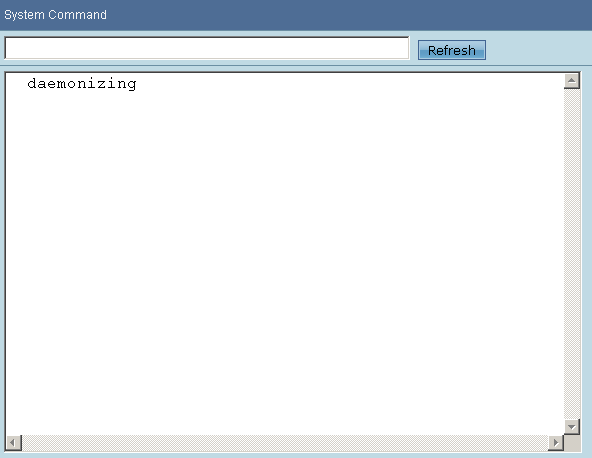
Now it is possible to connect to the router without a password via telnet protocol. To disable such an access you can from the web interface as well. To perform this you need to Refresh «killall utelnetd» command. It must be mentioned that telnet access fails after the reboot.
On entering the RT-N15 command line, we immediately face the brief information about the shell we work with. More detailed information about BusyBox will be displayed after entering the namesake command.
stdin, stdout, etderr: 0 1 2
BusyBox v1.4.2 (2009-03-05 10:29:07 CST) Built-in shell (ash)
Enter 'help' for a list of built-in commands.
/ # busybox
BusyBox v1.4.2 (2009-03-05 10:29:07 CST) multi-call binary
Copyright (C) 1998-2006 …Erik Andersen, Rob Landley, and others.
Licensed under GPLv2. …See source distribution for full notice.
Usage: busybox [function] [arguments]...
or: [function] [arguments]...
BusyBox is a multi-call binary that combines many common Unix
utilities into a single executable. Most people will create a
link to busybox for each function they wish to use and BusyBox
will act like whatever it was invoked as!
Currently defined functions:
[, [[, arp, ash, basename, cat, chmod, cp, date, diff,
dmesg, echo, egrep, fgrep, ftpget, grep, halt, ifconfig,
insmod, kill, killall, klogd, ln, logread, ls, lsmod,
mesg, mkdir, mkfifo, mknod, modprobe, more, mount, nslookup,
ping, ping6, poweroff, printf, ps, pwd, reboot, rm, rmmod,
route, sed, sh, sleep, syslogd, test, top, touch, traceroute,
umount, uname, uptime, vconfig, wc
The system runs a comparatively recent BusyBox version – 1.4.2. By the time the article was written 1.14.2 version of the shell had already existed.
Naturally, we were interested in other processes run on the router at the moment.
/ # ps
PID Uid VmSize Stat Command
1 0 544 S /sbin/init
2 0 SW [keventd]
3 0 SWN [ksoftirqd_CPU0]
4 0 SW [kswapd]
5 0 SW [bdflush]
6 0 SW [kupdated]
7 0 SW [mtdblockd]
15 0 SW [rtmpWscHandle]
38 0 312 S udhcpc -i eth2.2 -p /var/run/udhcpc0.pid -s /tmp/udhc
40 0 676 S /usr/sbin/httpd br0
41 0 540 S /usr/sbin/pppd file /tmp/ppp/options.wan0
42 0 308 S /usr/sbin/infosvr br0
43 0 340 S /sbin/syslogd -m 0 -t MST-3MDT -O /tmp/syslog.log
47 0 316 S /sbin/klogd
49 0 360 S /sbin/wanduckmain
51 0 344 S lld2d br0
52 0 396 S watchdog
53 0 348 S networkmap
54 0 384 S /bin/sh
55 0 360 S /usr/sbin/wanduck
56 0 364 S ntp
57 0 368 S ots
108 0 252 S /usr/sbin/utelnetd -d
109 0 424 S /bin/sh
111 0 332 R ps
Let’s see what commands are available in /bin, /sbin, usr/bin è usr/sbin catalogues.
/ # ls /bin
wscd ps iwpriv egrep
uname ping6 iwconfig echo
umount ping iptables-save dmesg
touch mtd_write iptables-restore date
spicmd mount iptables cp
sleep more igmpproxy.sh chmod
sh mknod igmpproxy cat
set8366s mkdir i2ccmd busybox
sed mii_mgr grep brctl
rt2860apd ls gpio ated
rm ln flash ash
reg lld2d fgrep
pwd kill ez-ipupdate
/ # ls /sbin
wsrom route halt
write175C rmmod gpio
write restore175C getSSID
wps_stop restore getPIN
wps_start reboot getMAC
wps_pin read175C getCountryCode
wps_pbc rc getChannel
wps_oob radioctrl getBootV
wmac pspfix gen_ralink_config
watchdog poweroff gbr
wanduckmain ots gbe
wan-up nvram_restore erase
wan-down ntp ddns_updated
vconfig modprobe convert_asus_values
syslogd lsmod config8366s
stopservice logread config175C
start_ddns klogd ateshow
startWan ip-up atehelp
speedtest ip-down asuscfe
setPIN insmod arp
setMAC init FWRITE
setCountryCode ifconfig
rsrom hotplug
/ # ls /usr/bin
wc top nslookup killall basename
uptime test mkfifo ftpget [[
traceroute printf mesg diff [
/ # ls /usr/sbin
wanduck udhcpc pppoe-relay networkmap httpd
utelnetd tc pppd l2tpd dproxy
upnp pptp.sh nvram l2tp-control bpalogin
udhcpd pptp ntpclient infosvr
Now we go to /proc catalogue to see what kind of files exist here.
/ # cd proc
/proc #
/proc # ls
116 47 3 interrupts iomem bus
109 43 2 filesystems partitions irq
108 42 1 dma slabinfo misc
57 41 self cmdline ksyms rt2880
56 40 loadavg locks kcore pci
55 38 uptime swaps net mtd
54 15 meminfo execdomains sysvipc Config
53 7 version mounts sys
52 6 modules kmsg fs
51 5 stat cpuinfo driver
49 4 devices ioports tty
/proc # cat version
Linux version 2.4.30 (root@magic_pan) (gcc version 3.3.6) #1953 2009õ╣┤ 04öÜÈ 14ö×å öØßöÜßô║Ì 09:33:06 CST
Let’s estimate how RT-N15 is loaded. For this purpose, we examine the content of uptime and loadavg files. In cat uptime output there are two numbers that correspond to uptime and idle time of the router. The first three numbers in cat loadavg output show the average load of the device for the last 1, 5 and 15 minutes. As we can see, at this moment our router is not loaded at all.
/proc # cat uptime
1617.67 1557.85
/proc # cat loadavg
0.00 0.00 0.00 1/25 119
As the most part of the electronics is covered with protecting screens, it will be interesting to find out what kind of processor is used in the router via the cat cpuinfo command, the output of which is displayed below.
/proc # cat cpuinfo
system type : Palmchip Surfboard
processor : 0
cpu model : unknown V6.12
BogoMIPS : 265.42
wait instruction : no
microsecond timers : yes
tlb_entries : 16
extra interrupt vector : yes
hardware watchpoint : no
VCED exceptions : not available
VCEI exceptions : not available
Here we end the once-over of the router command line and pass on to the testing.
Testing
We begin our tests with determining the device boot time, which means the time interval between the moment of power connection and the return of the first ICMP echo-response. ASUS RT-N15 boots in 22 seconds, quite a good result.
The next step is to test the device on the security flaws. To perform this we scan the device with Positive Technologies XSpider 7.7 network analyzer (Demo build 3100) from the network local segment. We found five open ports: UDP-53 (DNS), TCP-80 (HTTP), TCP-5431 (HTTP), TCP-9998 (unavailable) and TCP-18017 (HTTP). The most interesting vulnerabilities are shown below.
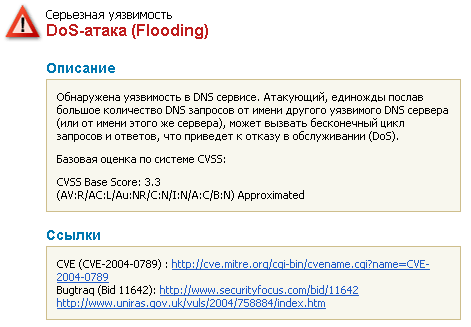
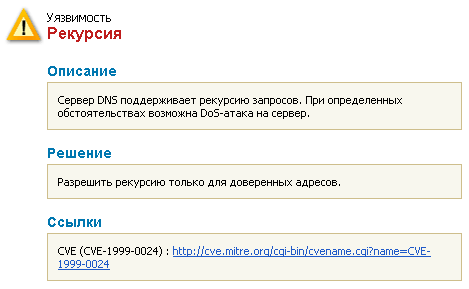
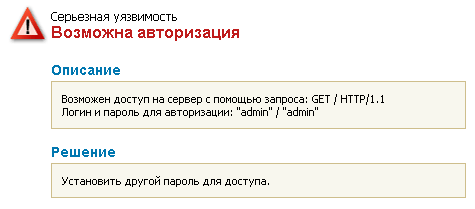
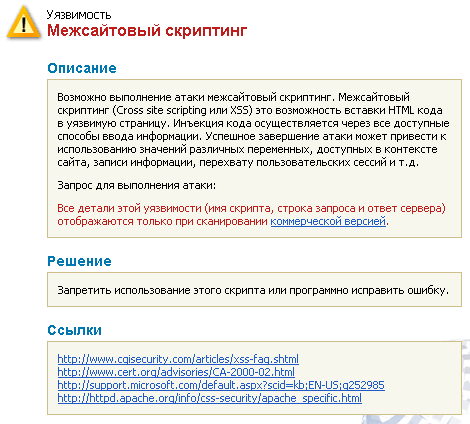
The detected availability of authentication via HTTP cannot be considered as a serious vulnerability as scanning was held when the router had default username and password. And one of the standard recommendations is to change them immediately.
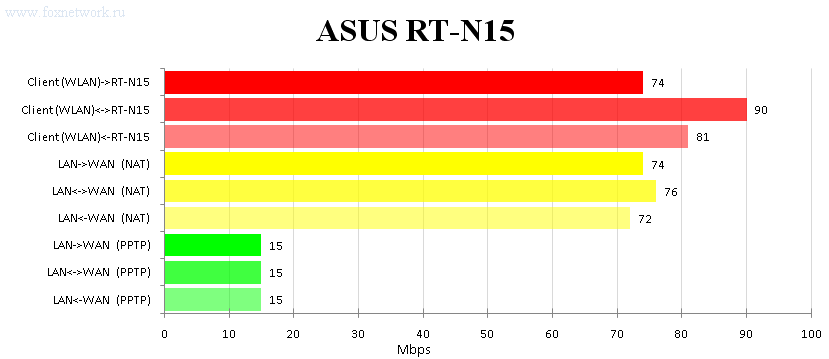
Now it’s time to test the speed of data transmission via RT-N15. Here we use netcps utility that to our mind is able to generate the traffic close to the real network. First of all, we tested the wireless data transmission speed. The transmission speed in any direction directly depended on the number of streams. The summarized speed achieved its high point at simultaneous transmission in both directions and was about 90 Mbps. The stream speed in the direction from the wireless client to the router was 74 Mbps and in the opposite direction it was 81 Mbps. All test results are displayed below. Then we decided to test the speed with which ASUS RT-N15 routes date. Here the difference was not so significant: in the direction from the global network to WAN interface the result was 72 Mbps, in the opposite direction – 74,4 Mbps and the summarized speed of simultaneous streams in both directions was 76 Mbps. We also didn’t forget about data transmission through the tunnel as among Russian providers such kind of internet access is the most common thing. Here speeds were equal, that is did not depend on the stream direction and were about 15 Mbps. The tunnel speed testing was held via PPTP without encryption at all.
We should say that we failed to set up PPTP encrypted tunnel and the process of setting up the tunnel without encryption was accompanied by various errors messages like “server is unavailable” or “incorrect dynamic address”. Yet, after the tunnel was up, everything went like clockwork.
|
Type |
Direction |
Speed, Mbps |
|
WLAN |
Client->RT-N15 |
74 |
|
Client<->RT-N15 |
90 |
|
|
Client<-RT-N15 |
81 |
|
|
NAT |
LAN->WAN |
74 |
|
LAN<->WAN |
76 |
|
|
LAN<-WAN |
72 |
|
|
PPTP |
LAN->WAN |
15 |
|
LAN<->WAN |
15 |
|
|
LAN<-WAN |
15 |
On the basis of the results a diagram was composed.
Of course, we can’t but mention the devices used in the test.
|
PC |
PC #1 |
PC #2 |
PC #3 |
|
Operation system |
Windows Vista SP2 x64 Ultimate Eng |
Windows XP SP2 x64 Eng |
Windows Server 2003 x32 SP2 Eng |
|
CPU |
Intel Pentium 4 3,0 GHz |
Intel Core 2 Duo 2,8 GHz |
Intel Pentium 4 3.2 GHz |
|
Motherboard |
Asus P5GDC Pro |
Asus P5K64 WS |
IBM M71IX |
|
Memory |
Hyundai 2 Gbyte (DDR2) |
OCZ 2 Gbyte (DDR3) |
Micron Technologies 1 Gbyte (DDR) |
|
NIC |
Marvell Yukon 88E8053, |
Marvell Yukon 88E8052/88E8001 |
Intel(R) PRO/1000 CT |
We finish the Test part here. Let’s make the conclusion.
Conclusion
On the whole, ASUS RT-N15 wireless router leaves a very good impression. Still, the vendor should pay more attention to the firmware testing as it really needs to be touched up, to our mind. The device strong points are listed below:
- good routing speeds (NAT and PPTP),
- strong defense against network attacks,
- WPS support,
- Russian language in the web interface,
- availability to enable/disable WI-FI module according to the time-schedule,
- IPTV support,
- dual data routing to internet and provider local network,
- availability for PPTP connection with the dynamic address of the interface.
We can’t but mention the weak points as well:
- bad reaction of the device on the restoration of the settings from the changed configuration file,
- absence of up to date documentation,
- rough Russian translation of the web interface,
- slow web interface,
- unfinished firmware.
We recommend RT-N15 for home network users with medium speed traffic.
By the time the article was written ASUS RT-N15 price in the Moscow internet shops was about 4700 rubles.
The author would like to publicly acknowledge the help of Andreeva Maria, who translated the article from Russian into English.